-->
Based on my experience, when running Microsoft Teams client on our computer, there are some background processes along with it. It is normal behavior, so you don’t need to worry about this. If you encounter any issue when using Microsoft Teams, feel free to post a new thread in our forum. Best Regards, Amanda. Microsoft Teams vs Slack daily usage chart. The reasons for such great enthusiasm are easily explained: MS Teams undoubtedly represents an excellent step forward, especially if we compare it to its previous iteration – Skype for Business, which will be retired on July 31, 2021, as explained by this announcement of the Microsoft Teams blog. Integrations for better collaboration 6. A picture’s worth a thousand words. And a diagram can communicate even more to your team. Cacoo is a collaborative diagramming app for modern teams and is especially useful for creating wireframes, flowcharts, mind maps, SWOT diagrams, network diagrams, UML diagrams, project timelines, and any other visual your team needs to bring their ideas.
Important
The Teams service model is subject to change in order to improve customer experiences. For example, the default access or refresh token expiration times may be subject to modification in order to improve performance and authentication resiliency for those using Teams. Any such changes would be made with the goal of keeping Teams secure and Trustworthy by Design.
Microsoft Teams, as part of the Microsoft 365 and Office 365 services, follows all the security best practices and procedures such as service-level security through defense-in-depth, customer controls within the service, security hardening and operational best practices. For full details, please see the Microsoft Trust Center.
Trustworthy by Design
Teams is designed and developed in compliance with the Microsoft Trustworthy Computing Security Development Lifecycle (SDL), which is described at Microsoft Security Development Lifecycle (SDL). The first step in creating a more secure unified communications system was to design threat models and test each feature as it was designed. Multiple security-related improvements were built into the coding process and practices. Build-time tools detect buffer overruns and other potential security threats before the code is checked in to the final product. Of course, it is impossible to design against all unknown security threats. No system can guarantee complete security. However, because product development embraced secure design principles from the start, Teams incorporates industry standard security technologies as a fundamental part of its architecture.
Trustworthy by Default
Network communications in Teams are encrypted by default. By requiring all servers to use certificates and by using OAUTH, TLS, Secure Real-Time Transport Protocol (SRTP), all Teams data is protected on the network.
How Teams Handles Common Security Threats
This section identifies the more common threats to the security of the Teams Service and how Microsoft mitigates each threat.
Compromised-Key Attack
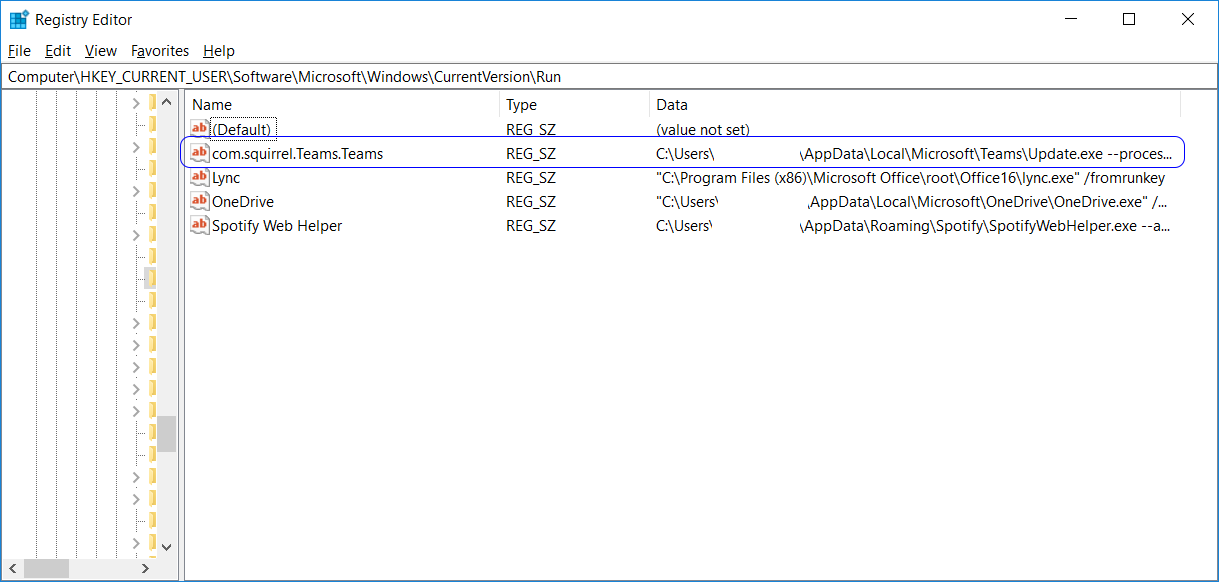
Microsoft Teams Process Names
Teams uses the PKI features in the Windows Server operating system to protect the key data used for encryption for the Transport Layer Security (TLS) connections. The keys used for media encryptions are exchanged over TLS connections.
Network Denial-of-Service Attack
The denial-of-service attack occurs when the attacker prevents normal network use and function by valid users. By using a denial-of-service attack, the attacker can:
- Send invalid data to applications and services running in the attacked network to disrupt their normal function.
- Send a large amount of traffic, overloading the system until it stops responding or responds slowly to legitimate requests.
- Hide the evidence of the attacks.
- Prevent users from accessing network resources.Teams mitigates against these attacks by running Azure DDOS network protection and by throttling client requests from the same endpoints, subnets, and federated entities.
Eavesdropping
Eavesdropping can occur when an attacker gains access to the data path in a network and has the ability to monitor and read the traffic. This is also called sniffing or snooping. If the traffic is in plain text, the attacker can read the traffic when the attacker gains access to the path. An example is an attack performed by controlling a router on the data path.
Teams uses mutual TLS (MTLS) for server communications within Microsoft 365 and Office 365, and also uses TLS from clients to the service, rendering this attack very difficult or impossible to achieve within the time period in which a given conversation could be attacked. TLS authenticates all parties and encrypts all traffic. This does not prevent eavesdropping, but the attacker cannot read the traffic unless the encryption is broken.
The TURN protocol is used for real time media purposes. The TURN protocol does not mandate the traffic to be encrypted and the information that it is sending is protected by message integrity. Although it is open to eavesdropping, the information it is sending (that is, IP addresses and port) can be extracted directly by simply looking at the source and destination addresses of the packets. The Teams service ensures that the data is valid by checking the Message Integrity of the message using the key derived from a few items including a TURN password, which is never sent in clear text. SRTP is used for media traffic and is also encrypted.
Identity Spoofing (IP Address Spoofing)
Spoofing occurs when the attacker determines and uses an IP address of a network, computer, or network component without being authorized to do so. A successful attack allows the attacker to operate as if the attacker is the entity normally identified by the IP address.
TLS authenticates all parties and encrypts all traffic. Using TLS prevents an attacker from performing IP address spoofing on a specific connection (for example, mutual TLS connections). An attacker could still spoof the address of the DNS server. However, because authentication in Teams is performed with certificates, an attacker would not have a valid certificate required to spoof one of the parties in the communication.
Man-in-the-Middle Attack
A man-in-the-middle attack occurs when an attacker reroutes communication between two users through the attacker's computer without the knowledge of the two communicating users. The attacker can monitor and read the traffic before sending it on to the intended recipient. Each user in the communication unknowingly sends traffic to and receives traffic from the attacker, all while thinking they are communicating only with the intended user. This can happen if an attacker can modify Active Directory Domain Services to add his or her server as a trusted server or modify Domain Name System (DNS) to get clients to connect through the attacker on their way to the server.
Man-in-the-middle attacks on media traffic between two endpoints participating in Teams audio, video, and application sharing, is prevented by using SRTP to encrypt the media stream. Cryptographic keys are negotiated between the two endpoints over a proprietary signaling protocol (Teams Call Signaling protocol) which leverages TLS 1.2 and AES-256 (in GCM mode) encrypted UDP / TCP channel.
RTP Replay Attack
A replay attack occurs when a valid media transmission between two parties is intercepted and retransmitted for malicious purposes. Teams uses SRTP in conjunction with a secure signaling protocol that protects transmissions from replay attacks by enabling the receiver to maintain an index of already received RTP packets and compare each new packet with those already listed in the index.
Spim
Spim is unsolicited commercial instant messages or presence subscription requests, like spam, but in instant message form. While not by itself a compromise of the network, it is annoying in the least, can reduce resource availability and production, and can possibly lead to a compromise of the network. An example of this is users spimming each other by sending requests. Users can block each other to prevent this, but with federation, if a coordinated spim attack is established, this can be difficult to overcome unless you disable federation for the partner.
Viruses and Worms
A virus is a unit of code whose purpose is to reproduce additional, similar code units. To work, a virus needs a host, such as a file, email, or program. Like a virus, a worm is a unit of code that is coded to reproduce additional, similar code units, but that unlike a virus does not need a host. Viruses and worms primarily show up during file transfers between clients or when URLs are sent from other users. If a virus is on your computer, it can, for example, use your identity and send instant messages on your behalf. Standard client security best practices such as periodically scanning for viruses can mitigate this issue.
Security Framework for Teams
This section gives an overview of fundamental elements that form a security framework for Microsoft Teams.
Core elements are:
- Azure Active Directory (Azure AD), which provides a single trusted back-end repository for user accounts. User profile information is stored in Azure AD through the actions of Microsoft Graph.
- Be advised that there may be multiple tokens issued which you may see if tracing your network traffic. This includes Skype tokens you might see in traces while looking at chat and audio traffic.
- Transport Layer Security (TLS), and mutual TLS (MTLS) which encrypt instant message traffic and enable endpoint authentication. Point-to-point audio, video, and application sharing streams are encrypted and integrity checked using Secure Real-Time Transport Protocol (SRTP). You may also see OAuth traffic in your trace, particularly around negotiating permissions while switching between tabs in Teams, for example to move from Posts to Files. For an example of the OAuth flow for tabs, please see this document.
- Teams uses industry-standard protocols for user authentication, wherever possible.
The next sections discuss some of these core technologies.
Azure Active Directory
Azure Active Directory functions as the directory service for Microsoft 365 and Office 365. It stores all user directory information and policy assignments.
CRL Distribution Points
Microsoft 365 and Office 365 traffic takes place over TLS/HTTPS encrypted channels, meaning that certificates are used for encryption of all traffic. Teams requires all server certificates to contain one or more Certificate Revocation List (CRL) distribution points. CRL distribution points (CDPs) are locations from which CRLs can be downloaded for purposes of verifying that the certificate has not been revoked since the time it was issued and the certificate is still within the validity period. A CRL distribution point is noted in the properties of the certificate as a URL and is secure HTTP. The Teams service checks CRL with every certificate authentication.
Enhanced Key Usage
All components of the Teams service require all server certificates to support Enhanced Key Usage (EKU) for the purpose of server authentication. Configuring the EKU field for server authentication means that the certificate is valid for the purpose of authenticating servers. This EKU is essential for MTLS.
TLS and MTLS for Teams
TLS and MTLS protocols provide encrypted communications and endpoint authentication on the Internet. Teams uses these two protocols to create the network of trusted servers and to ensure that all communications over that network are encrypted. All communications between servers occur over MTLS. Any remaining or legacy SIP communications from client to server occur over TLS.
TLS enables users, through their client software, to authenticate the Teams servers to which they connect. On a TLS connection, the client requests a valid certificate from the server. To be valid, the certificate must have been issued by a Certificate Authority (CA) that is also trusted by the client and the DNS name of the server must match the DNS name on the certificate. If the certificate is valid, the client uses the public key in the certificate to encrypt the symmetric encryption keys to be used for the communication, so only the original owner of the certificate can use its private key to decrypt the contents of the communication. The resulting connection is trusted and from that point is not challenged by other trusted servers or clients.
Server-to-server connections rely on mutual TLS (MTLS) for mutual authentication. On an MTLS connection, the server originating a message and the server receiving it exchange certificates from a mutually trusted CA. The certificates prove the identity of each server to the other. In the Teams service, this procedure is followed.
TLS and MTLS help prevent both eavesdropping and man-in-the middle attacks. In a man-in-the-middle attack, the attacker reroutes communications between two network entities through the attacker's computer without the knowledge of either party. TLS and Teams' specification of trusted servers mitigate the risk of a man-in-the middle attack partially on the application layer by using encryption that is coordinated using the Public Key cryptography between the two endpoints. An attacker would have to have a valid and trusted certificate with the corresponding private key and issued to the name of the service to which the client is communicating to decrypt the communication.
Note
Teams data is encrypted in transit and at rest in Microsoft datacenters. Microsoft uses industry standard technologies such as TLS and SRTP to encrypt all data in transit between users' devices and Microsoft datacenters, and between Microsoft datacenters. This includes messages, files, meetings, and other content. Enterprise data is also encrypted at rest in Microsoft datacenters, in a way that allows organizations to decrypt content if needed, to meet their security and compliance obligations, such as eDiscovery.
Encryption for Teams
Teams uses TLS and MTLS to encrypt instant messages. All server-to-server traffic requires MTLS, regardless of whether the traffic is confined to the internal network or crosses the internal network perimeter.
This table summarizes the protocols used by Teams.
Traffic Encryption
| Traffic type | Encrypted by |
|---|---|
| Server-to-server | MTLS |
| Client-to-server (ex. instant messaging and presence) | TLS |
| Media flows (ex. audio and video sharing of media) | TLS |
| Audio and video sharing of media | SRTP/TLS |
| Signaling | TLS |
Media Encryption
Media traffic is encrypted using Secure RTP (SRTP), a profile of Real-Time Transport Protocol (RTP) that provides confidentiality, authentication, and replay attack protection to RTP traffic. SRTP uses a session key generated by using a secure random number generator and exchanged using the signaling TLS channel. Client to Client media traffic is negotiated through a Client to Server connection signaling, but is encrypted using SRTP when going direct Client to Client.
Teams uses a credentials-based token for secure access to media relays over TURN. Media relays exchange the token over a TLS-secured channel.
FIPS
Teams uses FIPS (Federal Information Processing Standard) compliant algorithms for encryption key exchanges. For more information on the implementation of FIPS, please see Federal Information Processing Standard (FIPS) Publication 140-2.
User and Client Authentication
A trusted user is one whose credentials have been authenticated by Azure AD in Microsoft 365 or Office 365.
Authentication is the provision of user credentials to a trusted server or service. Teams uses the following authentication protocols, depending on the status and location of the user.
- Modern Authentication (MA) is the Microsoft implementation of OAUTH 2.0 for client to server communication. It enables security features such as Multi-Factor Authentication and Conditional Access. In order to use MA, both the online tenant and the clients need to be enabled for MA. The Teams clients across PC and mobile, as well as the web client, all support MA.
Note
If you need to brush up on Azure AD authentication and authorization methods, this article's Introduction and 'Authentication basics in Azure AD' sections will help.
Teams authentication is accomplished through Azure AD and OAuth. The process of authentication can be simplified to:
- User Login > Token issuance > subsequent request use issued token.
Requests from client to server are authenticated and authorized via Azure AD with the use of OAuth. Users with valid credentials issued by a federated partner are trusted and pass through the same process as native users. However, further restrictions can be put into place by administrators.
For media authentication, the ICE and TURN protocols also use the Digest challenge as described in the IETF TURN RFC.
Windows PowerShell and Team Management Tools
In Teams, IT Admins can manage their service via the Microsoft 365 admin center or by using Tenant Remote PowerShell (TRPS). Tenant admins use Modern Authentication to authenticate to TRPS.
Configuring Access to Teams at your Internet Boundary
For Teams to function properly (for users to be able to join meetings etc.), customers need to configure their internet access such that outbound UDP and TCP traffic to services in the Teams cloud is allowed. For more details, see here: Office 365 URLs and IP address ranges.
UDP 3478-3481 and TCP 443
The UDP 3478-3481 and TCP 443 ports are used by clients to request service for audio visuals. A client uses these two ports to allocate UDP and TCP ports respectively to enable these media flows. The media flows on these ports are protected with a key that is exchanged over a TLS protected signaling channel.
Federation Safeguards for Teams
Federation provides your organization with the ability to communicate with other organizations to share IM and presence. In Teams federation is on by default. However, tenant admins have the ability to control this via the Microsoft 365 admin center.
Addressing Threats to Teams Meetings
There are two options to control who arrives in Teams meetings and who will have access to the information you present.
You can control who joins your meetings through settings for the lobby.
'Who can bypass the lobby' setting options available in Meeting options page User types joining the meeting directly User types going to the lobby People in my organization - In-tenant
- Guest of tenant- Federated
- Anonymous
- PSTN dial-inPeople in my organization and trusted organizations - In-tenant
- Guest of tenant
- Federated- Anonymous
- PSTN dial-inEveryone - In-tenant
- Guest of tenant
- Federated Anonymous
- PSTN dial-inThe second way is through structured meetings (where Presenters can do about anything that should be done, and attendees have a controlled experience). After joining a structured meeting, presenters control what attendees can do in the meeting.
Actions Presenters Attendees Speak and share their video Y Y Participate in meeting chat Y Y Change settings in meeting options Y N Mute other participants Y N Remove other participants Y N Share content Y N Admit other participants from the lobby Y N Make other participants presenters or attendees Y N Start or stop recording Y N Take control when another participant shares a PowerPoint Y N
Teams provides the capability for enterprise users to create and join real-time meetings. Enterprise users can also invite external users who do not have an Azure AD, Microsoft 365, or Office 365 account to participate in these meetings. Users who are employed by external partners with a secure and authenticated identity can also join meetings and, if promoted to do so, can act as presenters. Anonymous users cannot create or join a meeting as a presenter, but they can be promoted to presenter after they join.
For Anonymous users to be able to join Teams meetings, the Participants meetings setting in the Teams Admin Center must be toggled on.
Note
The term anonymous users means users that are not authenticated to the organizations tenant. In this context all external users are considered anonymous. Authenticated users include tenant users and Guest users of the tenant.
Enabling external users to participate in Teams meetings can be very useful, but entails some security risks. To address these risks, Teams uses the following additional safeguards:
Participant roles determine meeting control privileges.
Participant types allow you to limit access to specific meetings.
Scheduling meetings is restricted to users who have an AAD account and a Teams license.
Anonymous, that is, unauthenticated, users who want to join a dial-in conference, dial one of the conference access numbers. If the 'Always allow callers to bypass the lobby' setting is turned On then they also need to wait until a presenter or authenticated user joins the meeting.
Caution
If you do not wish for Anonymous users (users you don't explicitly invite) to join a meeting, you need to ensure the Anonymous users can join a meeting is set to Off for the Participant meeting section.
It's also possible for an organizer to configure settings to let Dial-in callers be the first person in a meeting. This setting is configured in the Audio Conferencing settings for users and would apply to all meetings scheduled by the user.
Note
For more information on Guest and External Access in Teams, see this article. It covers what features guest or external users can expect to see and use when they login to Teams.
If you're recording meetings and want to see a permissions matrix around accessing the content, consult this article and its matrix.
Participant Roles
Meeting participants fall into three groups, each with its own privileges and restrictions:
- Organizer The user who creates a meeting, whether impromptu or by scheduling. An organizer must be an authenticated in-tenant user and has control over all end-user aspects of a meeting.
- Presenter A user who is authorized to present information at a meeting, using whatever media is supported. A meeting organizer is by definition also a presenter and determines who else can be a presenter. An organizer can make this determination when a meeting is scheduled or while the meeting is under way.
- Attendee A user who has been invited to attend a meeting but who is not authorized to act as a presenter.
A presenter can also promote an attendee to the role of presenter during the meeting.
Participant Types
Meeting participants are also categorized by location and credentials. You can use both of these characteristics to decide which users can have access to specific meetings. Users can be divided broadly into the following categories:
- Users that belong to the tenant These users have a credential in Azure Active Directory for the tenant.a. People in my organization – These users have a credential in Azure Active Directory for the tenant. People in my organization includes invited Guest accounts.b. Remote users – These users are joining from outside the corporate network. They can include employees who are working at home or on the road, and others, such as employees of trusted vendors, who have been granted enterprise credentials for their terms of service. Remote users can create and join meetings and act as presenters..
- Users that do not belong to the tenant These users do not have credentials in Azure AD for the tenant.a. Federated Users - Federated users have valid credentials with federated partners and are therefore treated as authenticated by Teams, but are still external to the meeting organizer tenant. Federated users can join meetings and be promoted to presenters after they have joined the meeting, but they can't create meetings in enterprises with which they are federated.b. Anonymous Users - Anonymous users do not have an Active Directory identity and are not federated with the tenant.
Many meetings involve external users. Those same customers also want reassurance about the identity of external users before allowing those users to join a meeting. The next section describes how Teams limits meeting access to those user types that have been explicitly allowed, and requires all user types to present appropriate credentials when entering a meeting.
Participant Admittance
Caution
If you do not wish for Anonymous users (users you don't explicitly invite) to join a meeting, you need to ensure the Anonymous users can join a meeting is set to Off for the Participant meeting section.
In Teams, anonymous users can be transferred to a waiting area called the lobby. Presenters can then either admit these users into the meeting or reject them. When these users are transferred to the lobby, the presenter and attendees are notified, and the anonymous users must then wait until they are either accepted or rejected, or their connection times out.
By default, participants dialing in from the PSTN go directly to the meeting once an authenticated user joins the meeting, but this option can be changed to force dial-in participants to go to the lobby.
Meeting organizers control whether participants can join a meeting without waiting in the lobby. Each meeting can be set up to enable access using any one of the following methods:
The defaults are:
- People in my Organization - Everyone external to the organization will wait in the lobby until admitted.
- People from my organization and trusted organizations - Authenticated users and external users from Teams and Skype for Business domains that are in the external access allow list can bypass the lobby. All other users will wait in the lobby until admitted.
- Everyone - All meeting participants bypass the lobby once an authenticated user has joined the meeting.
Presenter Capabilities
Meeting organizers control whether participants can present during a meeting. Each meeting can be set up to limit presenters to any one of the following:
- People in my organization - All in tenant users, including guests, can present
- People in my organization and trusted organizations - All in tenant users, including guests, can present and external users from Teams and Skype for Business domains that are in the external access allow list can present.
- Everyone - All meeting participants are presenters.
Modify While Meeting is Running
It's possible to modify the meeting options while a meeting is on-going. The change, when saved, will impact the running meeting within seconds. It also effects any future occurrences of the meeting.
Related topics
Microsoft Teams Compliance is the processes around meeting legal, regulatory, or organizational policies. For example, regulatory compliance is:
- Regulations imposed through laws or regulatory frameworks, typically dependent on jurisdiction.
- Document example includes contracts, invoices, tax documents, employee files, and customer data.
- Other examples include data residency and meeting specific certification requirements.
Microsoft Teams compliance covers many topics across the Office 365 feature set. This approach is because Microsoft Teams brings together many Office 365 apps and services into a single user interface. To understand compliance, we need to look at overall Office 365 features. These features cover most applications available in Office 365 that are accessible through Teams. We also need to look at the compliance functionality available in each application. It sometimes differs from the features available in Office 365 overall.
In this article, we are going to supply an overview of all the compliance features used by Microsoft Teams. Security and managing access to data is undoubtedly a vital compliance topic. Because we have so much to cover, we are going to focus on the non-security components of compliance in this post.
Here is what we will cover:
- Firstly, we need to understand where Microsoft locates Microsoft Teams data. Where we find the information is where the compliance magic happens.
- Next, we are going to talk about how Microsoft licenses compliance features and the overall certifications. This cover both Microsoft Teams and Office 365 have.
- Then, another hot topic, which is data residency and how to meet those requirements.
- Then the newest kid on the block. Microsoft Teams Information Barriers.
Read These Related Posts!
There are two other essential Microsoft Teams compliance topics that we will not cover today. The reason is that they are so vital that they have dedicated posts. These are:
- Office 365 Retention and Records Management: How to ensure content is kept for a proper amount of time and not prematurely deleted. Also, how to delete content permanently when appropriate.
Where is Microsoft Teams Data Located?
As you may know by now, there is no data that sits in Microsoft Teams. What happens is Teams stores the data in other services and then surfaced visually in the Microsoft Teams user interface. This architecture is why it is imperative to understand the data location for Microsoft Teams compliance.
As an example, you cannot put a retention policy on an entire Microsoft Team and have it cover all the files, conversations, and other data. You must think about each component that’s in the Team and apply the compliance policy there.
As another example, if you want to apply retention to files in one-to-one chats, Teams stores them in OneDrive for Business. You would need to set a retention policy or a retention label to the user’s OneDrive.
Where is Teams Chat Data Located?
A copy of Teams Chats are stored in user mailboxes for compliance and eDiscovery purposes. If you have a one-on-one chat with somebody, Teams stores a copy of the conversation in each user’s Exchange mailbox. This information is in a hidden folder that can only be accessed by administrators and Office 365 search services.
A chat with a bot is technically the same as a chat with a human. Teams also stores a copy of these conversations in the hidden chat folder in each user’s Exchange mailbox.
If you share a file in a one-to-one chat or one-to-many chat, then it is going to be stored in a OneDrive folder. That location is where Microsoft Teams compliance will be managed.
/cdn.vox-cdn.com/uploads/chorus_image/image/66917674/Ad_hoc_and_scheduled_voice_and_video_meetings_right_from_within_Microsoft_Teams_1000x563.0.jpg)
Where is Teams Channel Data Located?
When you create a Microsoft Team, a few services are also provisioned to support it. Firstly, it creates an Office 365 Group. This Group manages the permissions for the Team, and it also has an Exchange Group Mailbox. Additionally, it creates a SharePoint site for the Team. This location is where files will be stored.
Teams stores a copy of all channel conversations in the Exchange group mailbox. See the section below on the Chat Substrate for additional information related to the chats and conversation service. Teams treats posts in the channel conversation created by a connector or bot the same as any other conversation.
When a user shares a file or image in a channel conversation, then Team stores the file SharePoint. This location is where we manage Microsoft Teams compliance. The SharePoint site has a library called Documents, with a folder for each Teams channel. The files tab in each channel shows documents that are in the corresponding channel folder. Because of this, when we upload a document via Teams or the SharePoint user interface will always appear in both places.
Teams also stores emails sent to a Microsoft Teams channel in the Documents library, in the channel folder. When you submit the first email, Teams will create a new folder called Email Messages, within the channel folder.
In addition to files, there is a Wiki tab in each Microsoft Team. TTeams stores the wiki data in a SharePoint document library called Teams Wiki Data. Again, each channel has a folder inside this library, and then each wiki page is stored as a .mht file inside the channel folder.
If you create a OneNote for the Team, then it will be stored in the SharePoint site in the Site Assets document library.
Where is Teams Meeting and Call Information Located?
Calendar invites are a particular case because there is a copy of it that’s in both the group calendar and exchange mailbox. There is also a copy in the user mailbox when they accept the meeting.
The Skype (or Teams) call itself is launched from the individual’s Exchange mailbox, which includes both voice and video calls. After the meeting, Teams stores a summary in the user’s mailbox. This location is where meeting and call information is managed for Microsoft teams compliance.
If you are using Microsoft Teams for VOIP calls, then all the information is driven from the user’s Exchange mailbox. Firstly, contacts are stored, and the company directory is stored or accessed through Exchange. Secondly, Teams stores any voicemails or transcripts in the user’s mailbox. Finally, the call history and summaries are also stored there.
Where is Other Microsoft Teams Data Stored?
Let us look at where Microsoft Teams stores other related data. We do this by breaking down this functionality into a list of features. We look at where the data is stored, and how you would apply Microsoft Teams compliance in the chart below.
If you are using Microsoft Teams with Exchange on-premises, please see this article. It details where Teams stores the data in these cases.
| Feature | Location | Compliance |
| Chats | Exchange - User Mailbox | Follows the Office 365 retention policy or label applied to Microsoft teams chats |
| Conversations | Exchange - Group Mailbox | Follows the Office 365 retention policy or label applied to Microsoft teams channels |
| Files in a 1:1 or group chat | OneDrive for Business | Follows the Office 365 retention policy or label applied to the user’s OneDrive |
| Files in a Team | SharePoint | Follows the Office 365 retention policy or label applied to the SharePoint site |
| Third party file integration | Within the 3rd party service | Third party service |
| Group email and calendar | Exchange - Group Mailbox | Follows the Office 365 retention policy or label applied to the Team Exchange group mailbox |
| Planner | Planner | No compliance functionality |
| PowerBI | Source data system | The service where the data resides would manage compliance policies, not PowerBI |
| Stream | Stream | No compliance features |
| Yammer | Yammer | No compliance features |
| Bots | Chat or Conversation in Teams | Follows the Office 365 retention policy or label applied to Microsoft Teams chats or conversations |
| Connectors | Conversation in Teams | Follows the Office 365 retention policy or label applied to Microsoft Teams conversations |
| Tabs | A tab provides a view to content that resides in another location | The service where the data resides would manage compliance policies |
Other Teams Locations
Here are a few more details about the areas we have not yet discussed.
- Third-Party File Integration: Teams can show files from a location outside of Office 365, such as Box or Dropbox. Compliance for the files would occur in the service for the location of the data, such as Box.
- Planner: Microsoft Planner can help you manage tasks and projects. There currently is no compliance functionality for Planner. However, in the Microsoft documentation for Office 365 Retention, there is a note. It says, “[retention policy] Support for content in Planner…is coming soon”.
- Power BI: Power BI is a data dashboard tool. Given that, the data location is not Power BI, but in the database, Excel document, or another place where the data resides.
- Stream: Microsoft Stream is where video from Microsoft Teams recordings is stored. There is no compliance or retention functionality available.
- Yammer: There is no current Yammer functionality. But the note in the Retention documentation linked in the Planner bullet says it is coming soon.
- Tabs: A tab simply provides a view into content located in an app or service. That service would govern the data displayed in the tab.
The Microsoft Teams Chat Substrate
For compliance purposes, it is essential to understand how Microsoft Teams processes chat data. Teams uses an Azure-powered chat service that technically stores chat and channel messages. Only a copy of chats and conversations are kept in the user mailbox for compliance purposes. By default, this service stores the information forever.
Because of this, you will need to use Office 365 retention policies to remove Teams chats and conversations data. Otherwise, if you only delete them from the UI they will still exist in the chat service and possibly the mailbox if the data is retained, where we can find it through Content Search for eDiscovery. Using an Exchange policy will not remove Teams chats and conversations data. For Microsoft Teams compliance purposes you will want to completely remove the data.
The diagram below is from the Microsoft article “Overview of security and compliance in Microsoft Teams.”
How Office 365 Compliance Features are Licensed
Next, let us look at how Microsoft Teams compliance is licensed. Office 365 licensing is essential to understand. This is because some of the features we refer to in this article aren’t going to be available unless you have the right license. Some need either an E5 license or the Office 365 Advanced Compliance SKU.
The Advanced Compliance SKU is an add on that you can buy if you have Office or Microsoft 365 E3 license and you do not want to buy the entire E5 license. The Advanced Compliance SKU includes the compliance features we are discussing today. It does not include other E5 functionality.
The diagram above shows you what I consider to be compliance features. I got the image from Aaron Dinnage’s GitHub project and modified it for this purpose.
Microsoft and Office 365 E3 Compliance Functionality:
- Retention Policy includes basic retention functionality, such as creating retention labels and policies.
- Data Loss Prevention protects sensitive data in SharePoint, Office 365 Groups, and OneDrive.
- We cover Audit Logging in the linked article (coming soon).
- We cover eDiscovery in the linked article (coming soon).
Microsoft and Office 365 E5 Compliance Functionality and the Office 365 Advanced Compliance SKU:
- Customer Key controls your organization’s encryption keys. You then configure Office 365 to use them to encrypt your data at rest in Microsoft’s data centers.
- Customer Lockbox ensures that Microsoft cannot access your content to perform a service operation without your explicit approval.
- Privileged access management allows granular access control over privileged admin tasks in Office 365.
- Advanced Message Encryption helps customers meet compliance obligations that require more flexible controls over external recipients and their access to encrypted emails.
- Advanced Data Governance covers many compliance features, such as the automatic application of retention labels and policies, disposition review, file plan manager, event-based retention, and more.
- We cover Advanced eDiscovery in the linked article (coming soon).
- Data Loss Prevention for Teams: allows you to protect sensitive information in chats and channels.
- We cover Information Barriers in the section below.
How Office 365 Compliance is Certified
When we think about compliance and Office 365, it is vital to understand how Microsoft certifies their different services. Microsoft has different tiers of compliance certification that are labeled A, B, C, and D. These are important to understand for Microsoft Teams compliance.
The chart above comes from the Compliance Framework for Office 365 whitepaper from Microsoft. You can see in the table what certifications or commitments they have met for each one of the tiers.
Tier D has the strictest requirements, meeting the commitments listed in tiers A-D. Microsoft Teams and all the related services are Tier D compliant. To look a little more into that, you can see when we highlight all the features that are in Microsoft Teams; they are all our Tier D compliant except for Planner.
Microsoft Teams Data Residency
What is data residency? Data residency refers to the physical or geographic location of an organization’s data or information. If you are an existing Office 365 customer, you can look at where your data is found at rest right now. The location of your data is important to understand for Microsoft Teams compliance.
Here is how you find the location of your Office 365 data. You must be a tenant administrator.
- Browse to Office 365 Tenant Administration.
- Click on settings > organizational profile > data location.
Here you can see where Microsoft locates your Exchange, SharePoint, Skype for Business, and Microsoft Teams data.
If you are not an existing Office 365 customer, or if you have not started to use one of these services, there is a different tool you can use. By the way, “using Microsoft Teams” is defined as one user from your tenant has logged into Microsoft Teams.
The Office 365 data location map allows you to view where all the Microsoft data centers exist in the world. You can also see what services are provided by each data center. This helps you meet your Microsoft Teams compliance residency needs.
To use the data location tool, follow these steps.
- Navigate to https://products.office.com/en-us/where-is-your-data-located.
- Select your company location, OR your geography.
- It shows the available data centers along with the exact location for data at rest for Office 365 and Azure.
Your data will always be replicated between two data centers to ensure redundancy for up time.
Data Residency Example for Microsoft Teams
Let us say you are a government organization located in Australia. You have a law with which you need to comply that says all government data must stay in Australia. Here are the steps you will need to follow to enable multi-geo.
- Purchase the Multi-Geo Capabilities in Office 365 service plan from Microsoft.
- Enable Multi-Geo in Exchange and SharePoint.
- Set the PreferredDataLocation (PDL) for each user in Azure connect.

Once you complete these steps, here is what will happen when a user creates a new Microsoft Team:
- A user in Australia clicks create Team.
- An Office 365 Group is created in Australia because that is the user’s PDL.
- The Office 365 Group creates the Exchange Group Mailbox.
- It creates a SharePoint site in Australia based on the PDL.
- The user’s OneDrive and Exchange mailbox are already located in Australia for teams chats.
If you need to move existing Exchange Mailboxes and SharePoint sites (and therefore existing Teams data) to different geography, you can follow these instructions.
Microsoft Teams Information Barriers
Process Name For Microsoft Teams
Our final topic is Microsoft Teams information barriers. Information Barriers prevent individuals or groups from chatting with one another or sharing documents. Information barriers are important for Microsoft Teams compliance in some organizations. When we authored this article, information barriers are still in preview and is not generally available.
Microsoft does not yet support Information barriers for SharePoint and OneDrive file collaboration. However, that is coming soon. Microsoft has not announced a date yet for this release, but it’s something they call very clearly in the documentation.
If you want to manage these policies, you will need to use the PowerShell cmdlets, and I have the documentation for that linked here.
Microsoft Teams Process Name
Now you know everything about Microsoft Teams compliance! Please add your questions in the comments.